Everything your business needs to know about DDoS attacks
April 15, 2025
|
6
min read

Highlights
Facing downtime or network slowdowns? DDoS attacks are on the rise, and no business is immune. Learn what they are, why you're at risk, and how to defend your business against cyber disruption.
“OK. So… exactly what is a DDoS attack?” Unfortunately, it’s a question being asked with increasing regularity by owners and CEOs confronted with the news that their systems have suffered an attack.
DDoS (Distributed Denial-of-Service) attacks pose a constant and escalating threat to all businesses. According to cyber security training platform StationX, between 2020 and 2022 cyber attacks against SMEs surged by 150%, reaching 31,000 attacks per day globally. A 2025 roundup of cyber crime statistics from one of the UK’s leading managed services firms, meanwhile, revealed that enterprise organisations undergo an eyewatering 1700 attacks each day. Regardless of size, it’s important for all businesses to understand how DDoS attacks work, what their impact might be and, most importantly, how to prevent DDoS attacks.
We’ve put together this guide to help you understand the fundamentals of DDoS attacks, the types businesses face, why they are targeted, and the best strategies for prevention and mitigation. And we’ll also look at how Vorboss can help you safeguard your operations and prevent DDoS attacks from succeeding.
What is a DDoS attack?
A DDoS attack aims to overwhelm a system, service, or network with excessive internet traffic, leaving it inaccessible to legitimate users. In business terms, the consequences can be extremely serious, leading to financial loss, reputational damage and substantial disruption to operations.
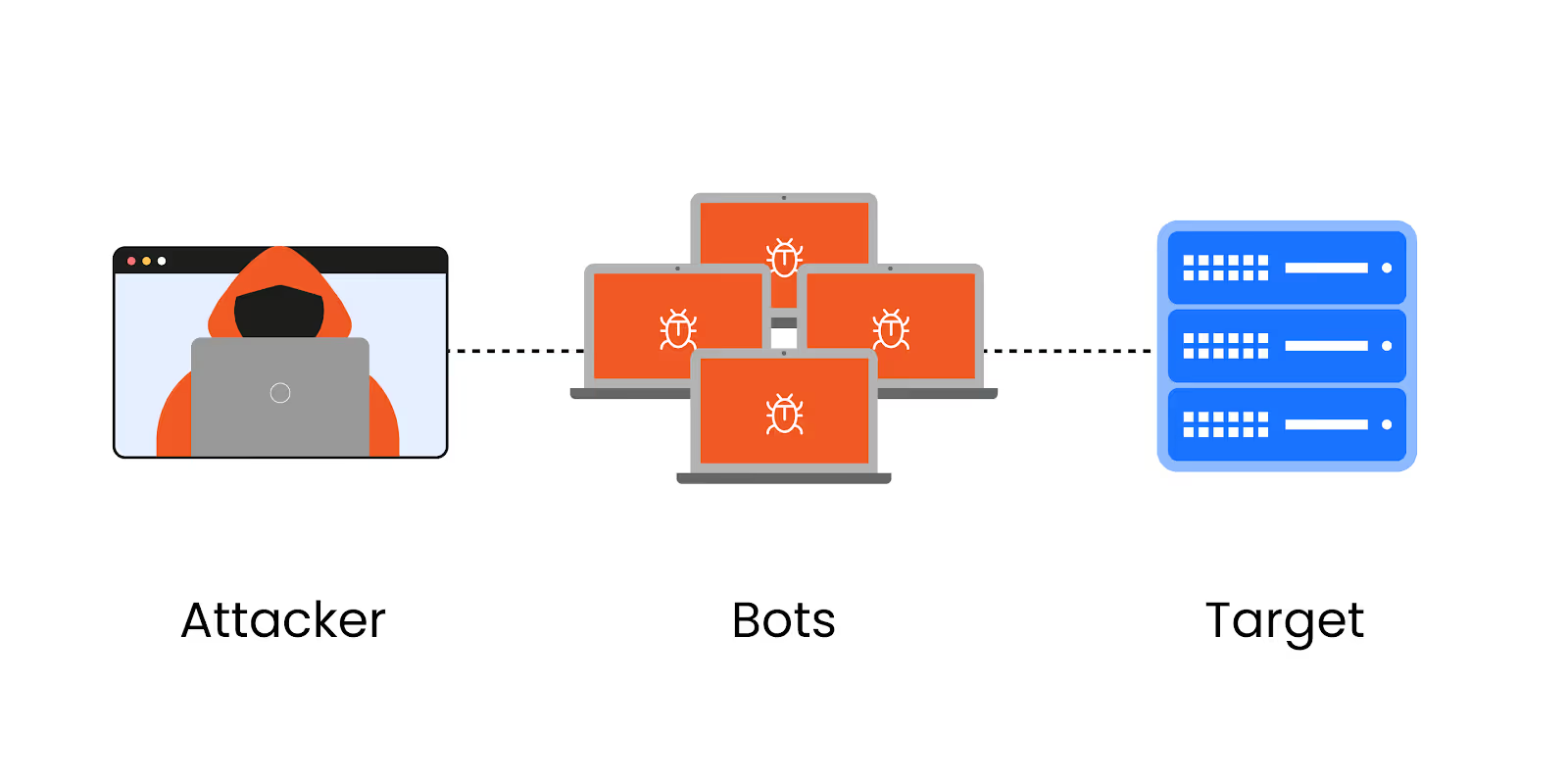
So what’s the difference between a DoS and DDoS attack, as both terms are often mentioned when a business has been affected? In a traditional DoS (Denial-of-Service) attack, a single system is usually involved in launching the attack. A DDoS attack, in contrast, leverages multiple compromised computers, often distributed globally, to create a coordinated assault. These devices form what is known as a botnet - an army of infected machines controlled by a malicious actor whose agenda may range from the criminal to the pointlessly disruptive.
Now let’s try to answer the question, “What are DDoS attacks?” at a technical level. Typically, DDoS attacks work by exploiting weaknesses in internet-connected systems, using a range of techniques to flood the target with requests.
Attackers may direct massive amounts of data at a server to exhaust its bandwidth, send malformed network packets to confuse and crash the system, or target vulnerabilities in applications to bring them down. Because the traffic appears to come from many different sources, blocking the attack is much more complex than dealing with a single-source DoS attack.
There are also some common misconceptions about what DDoS attacks are. One of these is that only large companies are really at risk. In reality, businesses of all sizes are targeted all the time, including small and medium enterprises.
Another misconception is that firewalls alone provide adequate protection. While firewalls play an important role in network security, they are not designed to handle the sheer scale of a DDoS attack. People also often assume that a DDoS attack would be immediately noticeable. Many attacks begin subtly, however, gradually increasing in intensity over time. This makes early detection and mitigation a critical part of how to prevent DDoS attacks.
Types of DDoS attacks
DDoS attacks come in several forms, each with its own approach to overwhelming a system. With IBM’s 2024 Cost of a Data Breach Report revealing that the global average cost of a data breach (across both enterprise and SMB targets) had reached $4.88 million, it’s worth being aware of the different attack types, so you can take targeted action to defend against them.
Volumetric Attacks
Volumetric attacks are among the most common and straightforward forms of DDoS attacks. They work by consuming all the available bandwidth between the target system and the rest of the internet, so that the system has no capacity to handle legitimate users or customers.

Because of their scale, these attacks can be devastating, with the total amount of data being directed at the target system sometimes reaching trillions of bits per second in intensity - far beyond what most networks are designed to handle. The way that attackers achieve this is by generating a massive flood of data requests, often using the botnets described earlier to amplify their impact. Examples of volumetric type attacks include UDP floods, ICMP floods, and DNS amplification attacks.
To combat volumetric attacks, businesses need robust traffic filtering solutions, content delivery networks (CDNs), and scalable network infrastructure that’s capable of absorbing these kinds of sudden surge in demand.
Protocol Attacks
Protocol attacks, which are also known as state-exhaustion attacks, exploit vulnerabilities in network protocols to use up server resources. Unlike volumetric attacks that overwhelm bandwidth, protocol attacks specifically target weaknesses in the way devices and applications handle network connections. SYN floods, Ping of Death and Smurf attacks are all examples of this type of attack.

Protocol attacks can be difficult to detect because they don’t rely on massive traffic spikes. Instead, they stealthily take advantage of standard networking functions, causing a system to become sluggish or unresponsive. A business can mitigate these attacks using firewall rules, rate-limiting strategies and dedicated intrusion detection systems that monitor network activity for unusual patterns.
Application Layer Attacks
Application layer attacks, which are also known as Layer 7 attacks, are the most sophisticated and difficult kind of DDoS to detect. These attacks target the application or service layer of a system, mimicking legitimate requests but at a scale designed to overwhelm backend processes. Because they don’t generate massive volumes of traffic like volumetric attacks, they often outwit traditional detection methods.

One well-known example is the HTTP flood, where attackers send an overwhelming number of HTTP requests to a website, forcing the server to process each request until it becomes overloaded. Another Application Layer DDoS attack example is the Slowloris attack, where an attacker opens multiple connections to a target server and sends partial HTTP requests, keeping them open for as long as possible to consume server resources.
Application layer attacks are particularly dangerous because they target specific functions of a business’s digital services. A well-crafted attack can take down your login pages, API endpoints, or online transaction systems, disrupting essential operations in your business.
“How do I stop DDoS attacks of this kind?” Good question. Mitigation strategies include using web application firewalls (WAFs), traffic analysis tools and bot mitigation services to distinguish between human users and automated threats.
To develop an effective defence strategy, as at Vorboss we routinely do for customers, a business and its security partner need to understand the different types of DDoS attacks. By combining multiple layers of security - such as firewalls, traffic monitoring, and scalable infrastructure - you can significantly reduce your risk of falling victim to these disruptive cyber threats.
Why are businesses targeted by DDoS attacks?

What is the purpose of a DDoS attack? DDoS attacks happen for a variety of reasons, and you can find your business targeted no matter what industry it is in. Some attacks are financially motivated, while others are designed to cause disruption or make a statement.
Cybercriminals sometimes use DDoS attacks as a form of extortion. In what’s known as a ransom DDoS (RDoS) attack, the attacker demands payment in exchange for stopping or preventing the attack. Businesses that rely on uptime to generate revenue, such as e-commerce platforms or online services, may make the decision to comply rather than risk prolonged downtime.
As is always the case with blackmail, however, paying the ransom does not guarantee protection, and it can even mark the company out as a fruitful ‘repeat’ target for the future.
In some industries, businesses face attacks from competitors looking to cause disruption. A well-timed DDoS attack can take down a rival’s website or online services during a crucial period, such as a product launch or seasonal sales event. While this kind of corporate sabotage is both unethical and, in the UK under Section 3 of the Computer Misuse Act 1990, illegal, it’s certainly not unheard of - particularly in high-competition markets.
DDoS attacks are also used by what are known as ‘Hacktivist’ groups to target organisations they disagree with politically, socially, or ethically. These attacks are often launched against government departments, financial institutions, or businesses associated with controversial industries. Unlike financially motivated attacks, ideological attacks are typically intended to send a message rather than extract ransom.
To complicate things further, not all DDoS attacks have any clear purpose. ‘Random Opportunity Attacks’ are usually carried out simply because an attacker finds an easy target. Automated scripts and botnets constantly scan the internet for vulnerable systems, and if a business lacks proper security measures it can find itself victim of an attack for no real reason whatsoever. While such attacks may not have a specific goal, they can still cause serious damage to your business by disrupting operations, costing both time and money.
Impact of DDoS attacks on businesses
The consequences of a DDoS attack can be devastating. They can affect not only the immediate operational capacity of your business, but also its long-term stability and reputation.

Stats from dasher.com
Downtime and resultant loss of revenue are of primary concern if your business relies heavily on its online presence. If, for example, you run an e-commerce platform or are a financial institution or cloud service provider, disruptions can quickly translate into significant financial losses. Customers unable to access your services may seek alternatives, leading to lost sales and, potentially, long-term customer attrition.
DDoS attacks can also cause damage to your brand reputation. If you repeatedly experience outages your business can quickly gain a reputation for unreliability. In highly competitive markets, this can damage customer confidence and result in reduced market share, as clients and partners begin to view you as insecure or unstable.
Another significant possible impact is the breach of customer trust. Even if no data is stolen, customers expect services to be available when needed. Prolonged disruptions can create doubt in your company’s ability to protect its infrastructure and maintain security, making it harder both to retain existing customers and attract new ones.
Finally, the costs of recovery after a DDoS attack can be extensive. You may find yourselves needing to invest in forensic analysis, security upgrades, and potentially even legal compliance measures if an attack exposes weaknesses that lead to regulatory scrutiny. On top of this, there could be costs associated with customer compensation, public relations efforts and enhanced security infrastructure to prevent future attacks.
How to detect a DDoS attack?
Detecting a DDoS attack early is crucial if you are to minimise its impact. The first sign of an attack is often a sudden slowdown in the performance of your systems or an unexplained spike in traffic. You should be alert to signs such as your website taking longer than expected to load, your services becoming intermittently unavailable, or customers complaining about accessibility issues.
Using monitoring tools and techniques can help distinguish between normal fluctuations in traffic and a potential DDoS attack. Network monitoring solutions can analyse incoming traffic for unusual patterns, such as an unexpected influx of requests from unfamiliar regions or spikes in traffic targeting a specific part of a service. Some businesses implement ‘anomaly detection’ systems that use artificial intelligence to differentiate between legitimate and malicious traffic automatically.

One of the key challenges is distinguishing legitimate traffic surges from DDoS attacks. Seasonal sales, marketing campaigns or viral content can generate large amounts of desirable traffic that may look similar to an attack at first glance. However, legitimate traffic typically shows a natural pattern, while a DDoS attack often appears as a sustained and unnatural surge. Analysing traffic sources, request types, and behavioural patterns can help a business determine whether it’s under attack, or simply experiencing a welcome spike in customer activity.

How to protect your business from DDoS attacks
Vorboss has huge experience in providing businesses of every size with robust protection. So, having looked at what is a DDoS attack, and at how to detect when your business is being targeted, the most important questions are how to prevent DDoS attacks and mitigate their impact?
- The first line of defence is always a robust firewall, filtering incoming traffic to block malicious requests before they reach the network.
- Load balancing and content delivery networks (CDNs) help distribute traffic across multiple servers, preventing single points of failure. This approach enhances resilience against high-volume attacks.
- Conducting regular security audits ensures that vulnerabilities are identified and addressed before they can be exploited.
- It’s also good to develop and maintain an incident response plan, outlining the steps to be taken in the event that you are subject to an attack.
- Working with a trusted internet service provider like Vorboss can enhance protection, as many providers (Vorboss included) offer built-in DDoS mitigation services.
- If your ISP does not offer this, you can safeguard yourselves by using dedicated DDoS mitigation services, which provide real-time traffic analysis and automatic threat neutralisation.
- Finally, you should consider the benefits of automatic mitigation over manual mitigation. Automated systems use AI-driven detection and response, providing faster and more effective defence against attacks, whereas manual mitigation requires human intervention and can be slower to react
How Vorboss in safeguarding against DDoS attacks
When procuring business internet, London companies have a wide range of providers to choose from, but Vorboss provides robust security solutions designed to protect business customers from the growing threat of DDoS attacks. We leverage advanced threat detection and mitigation technologies to make sure customers maintain network uptime and security even in the face of large-scale attacks.
We employ real-time traffic monitoring and intelligent filtering to identify and block malicious traffic before it reaches our customers’ networks. Our automated DDoS mitigation systems detect unusual patterns and respond instantly, reducing downtime and preventing prolonged disruptions. Unlike traditional reactive approaches, Vorboss’s security solutions actively learn from each attempted attack, enhancing protection over time.
Choosing Vorboss as your security partner is a smart answer to the question of, “How do I stop DDoS attacks?”
Vorboss provides your business with enterprise-grade DDoS protection backed by a team of experienced cybersecurity experts. Our services include scalable mitigation solutions, ensuring you receive tailored protection no matter what the size of your business or infrastructure. As we integrate our DDoS protection with Vorboss’s high-performance internet services, this results in a seamless solution for any business that’s reliant on fast and uninterrupted connectivity.
By partnering with Vorboss, you gain peace of mind, knowing that your critical online infrastructure is protected from DDoS attacks, no matter what form they take.
Be Proactive. The answer to how to prevent a DDoS attack
DDoS attacks are a pressing issue, and a clear and present danger, for businesses of all sizes. Proactive measures such as implementing robust security solutions, conducting regular audits, and partnering with a reliable provider like Vorboss are the best way to minimise the risk and mitigate the impact of these threats. An effective defence strategy is not so much about recovering from an attack as about preventing it in the first place, protecting both your operations and reputation.
If your business is looking for comprehensive DDoS protection and uninterrupted network performance, get in touch with us. Contact Vorboss to learn how we can help protect your business from DDoS attacks with reliable and secure solutions.
Tell us about yourself so we can serve you best.
More articles

Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript

Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript

.avif)

.avif)

